SUSHI report: Adaptable Hardware for Security: That’s What Mr. Spock Would Do!
Talk by Prof. Ahmad-Reza Sadeghi from TU Darmstadt
 V’Ger credit: Michael Mundwiller
V’Ger credit: Michael MundwillerThis is report I wrote for the talk “Adaptable Hardware for Security: That’s What Mr. Spock Would Do!” at SUSHI Workshop: Sustainable Hardware Security, which co-locate with ICCAD 2022. The talk was given by Prof. Ahmad-Reza Sadeghi from TU Darmstadt.
Table of Contents
Introduction
From devices as small as intelligent bulbs to as large as electric cars, hardware is indispensable in modern civilization. Besides the convenience hardware brings to human lives, the rapid growth of the global semiconductor business also presents a number of questions about the security and reliability of information systems, which are becoming more and more crucial to the functioning of modern civilization. During the past decades, most security defenses in system security research have been mainly focused on the isolation of attackers from certain components of the system. Modern computer systems define protections in terms of privilege levels or protection rings. Systems are divided into layers and these layers form hierarchies, where lower layers have more privileges than higher layers and are isolated from higher layers. More specifically, the lowest level is usually the hardware such as the CPU; and one level up is the operating system, and then followed by applications that can be both benign and possibly malicious. The traditional methods against security attacks are either hardware isolation through specific hardware modules or software isolation such as virtualization. However, in recent years, a new attack paradigm becomes more attractive in the hardware security community, that hardware vulnerabilities can be exploited by local or remote unprivileged software. For instance, microarchitectural design flaws, information leakage, and implementation flaws in hardware may be found and abused by attackers. There are a lot of papers proposing new hardware vulnerabilities, some of them can be found in the figure below. Given that most nowadays hardware (instead of programmable hardware such as FPGA) cannot be changed post-fabrication, it requires thorough designs before putting into production to prevent potential attacks. Nevertheless, it is often the case that some new vulnerability will be found after the product is in use for a while, and the traditional isolation methods are not competent in addressing the security issues. Thus, new security approaches are demanded to overcome the current ad-hoc solution culture.
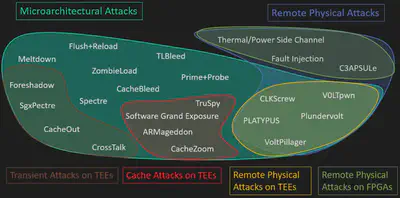
The V’Ger Problem
With a broader perspective beyond computer security, this type of attack paradigm does not come into being only in recent years. As an analogy, Star Trek, an American science fiction media franchise that dates back to the 1960s, describes a sentient and massive entity named V’Ger which threatened Earth in 2271. V’Ger destroyed everything on its path by digitizing it for its memory chamber. It was then found that it gained sentience after unknown alines repaired its cores, and surprisingly the core was the old Earth space probe Voyager 6! The huge vessel and everything of V’Ger were built and evolved from only the “old and inferior” Voyager 6, which is in a sense the vulnerability of V’Ger. In the background of hardware security, V’Ger’s story shows one example of building secure systems from insecure legacy systems, which is similar to the new hardware security issue at present.

Adaptable Platforms for Security
To protect from the new kind of attack paradigm, the adaptable platform is one of the promising methods. Similar to FPGA, the intuition behind adaptable platforms is to combine the flexibility of software with the high performance of hardware, as shown in the figure below. Rather than nearly fully programmable as FPGA, only the parts that may cause security issues are made configurable in adaptable platforms when considering security defenses. Therefore, the performance and implementation overhead can be maintained at a low level, and it is feasible to patch security vulnerabilities at any time when new flaws are found.
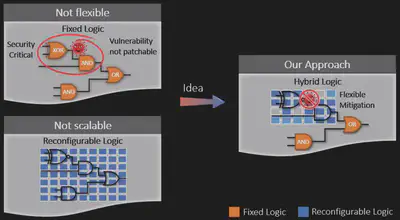
Though the vision is exciting, there are many challenges in designing secure and efficient adaptable hardware. The first one is to identify and map security-relevant elements to configurable units. In some sense, if all possible security issues are known beforehand, then there is no need to sacrifice the fixed logic for configurable logic, and thus without security issues, the smaller the configurable logic the better. It is because the hardware design cannot reach the acme of perfection from being attacked, the trade-off between security flexibility and performance exists. In addition to the first challenge, a further challenge is the optimization strategies for security, performance, power and area trade-off of configurable units. The third challenge is the validation of configuration strategies and vulnerability detection, also using novel hardware fuzzing methods.
Some preliminary results from the speaker may lay a solid foundation for the designs of adaptable platforms: novel configurable secure cache architecture [1], first step towards effective hardware fuzzing [2].
Reference
[1] Ghada Dessouky et al. Chunked-Cache: On-Demand and Scalable Cache Isolation for Security Architectures. 2021. doi: 10.48550/ARXIV.2110.08139. url: https://arxiv.org/abs/2110.08139.
[2] Aakash Tyagi et al. TheHuzz: Instruction Fuzzing of Processors Using Golden-Reference Models for Finding Software-Exploitable Vulnerabilities. 2022. doi: 10.48550/ARXIV.2201.09941. url: https://arxiv.org/abs/2201.09941.